Realistic Gmail Login Page Used in Clever Phishing Scam
March 23, 2017
Hitting the news this week is a story about a Gmail scam that was actually seen by Wordfence and reported on about two months ago. In this one, Gmail users may receive a message with an attachment. It looks like one you already received, but is actually just a thumbnail of that one. However, if it’s clicked a dialogue pops up asking you to enter your login credentials for your Gmail account again.
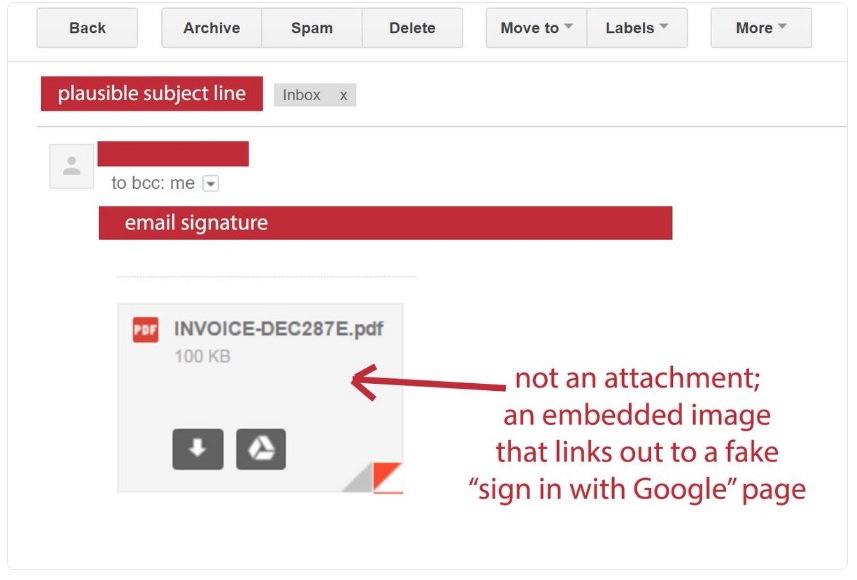
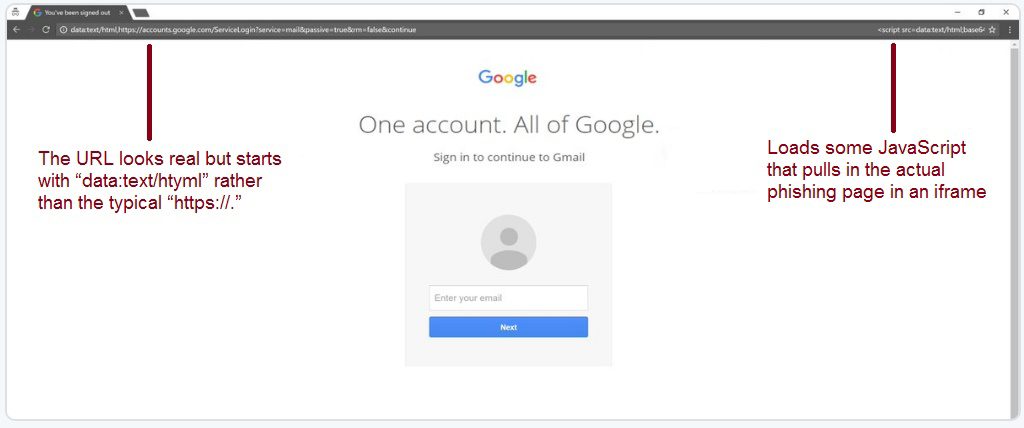
This one is ridiculously realistic and looks nearly, if not exactly identical to the actual Gmail login page. Even those who are very experienced at detecting phishing have had some difficulty with this one. The only difference is the URL which starts with “data:text/htyml” rather than the typical “https://.”
If you are asked to login again to any account after you already have logged in, especially after you clicked an attachment, eye it with suspicion. Then try following to avoid installing malware or giving someone access to your account that you don’t intend to:
-Click the “X” to close the window and log out of your account and then try again.
-If it doesn’t allow you to click an “X” to close it, shut your browser down and restart it. If it still gives you trouble, restart your computer.
-Change your password just for extra safety. Make sure it’s unique to this account. Do this before doing the next steps.
-Check the other connections to your account in your Google account activity page under My Account > Manage your Google Activity > Personal info & privacy > Connected apps & sites. That will list what other devices are using your account and you can disconnect the ones that are not familiar. Then restart your browser.
-Use multifactor authentication (MFA) that is offered by Google for Gmail. There are several options for this in your Google account settings. The most secure one, and possibly the “wave of the future” in MFA is a secure key. This is a tiny device that is inserted in the USB port of your computer. It authenticates to your Google or other accounts and unless someone has that key, your account will not work. Some keys also work with mobile devices and many other companies are supporting this now including Facebook and Dropbox.
-If none of the available MFA options work for you, take an extra moment to make sure that you see the secure login indicators in the browser when entering sensitive information such as passwords. This is the “lock” icon that usually precedes the address of the site and/or make sure it has “https://” in front of the domain name. It’s no longer a guarantee of a secure site, but it is much more likely to be.
In addition, make sure that if you are not expecting an attachment or link from anyone, verify that it is legitimate before clicking. It is very easy to make an email address appear that it came from someone you know, when it really didn’t. So if you receive something out of the blue, text or call the sender to make sure before clicking it.
In this scam, as soon as a password is entered into the fake login dialogue box, someone logs into the account and the attackers start perusing your messages.
They use documents in them to send icon images in messages to contacts in the address book. This makes it appear that the messages are coming from someone the recipients actually know. A recent study by Avecto found that 68% of survey participants would click links from someone they know without question. That makes a scam like this one likely to be successful. With a little bit of caution, you can help prevent that.
© Copyright 2017 Stickley on Security

